
Best Social Commerce Platforms in 2024

This article has been just updated:
We, humans, are social beings, so it’s only natural that we’ve always seen shopping as a social experience. We listen to the recommendations from people we trust, like to show off our purchases to friends and strangers alike, and we base our purchasing decisions on the social roles we assume.
The global e-commerce industry, whose sales amounted to $3.53 trillion in 2019, is increasingly becoming more social as well, coming up with new ways to satisfy the insatiable demand for social commerce.
If you’ve never heard the term social commerce before, you can be sure that you’ll hear it again and again in the future because it’s one of the largest e-commerce trends in 2024.
In the simplest terms, social commerce is any electronic commerce that involves social media.
Today, there are around 3 billion social media users, and 30 percent of them would like to make purchases directly through social media platforms.
By far the biggest advantage of social commerce compared with the traditional e-commerce experiences most of us are used to is its efficiency. The average user spends 2 hours and 33 minutes per day on social media, posting updates, reading what others are up to, and browsing products.
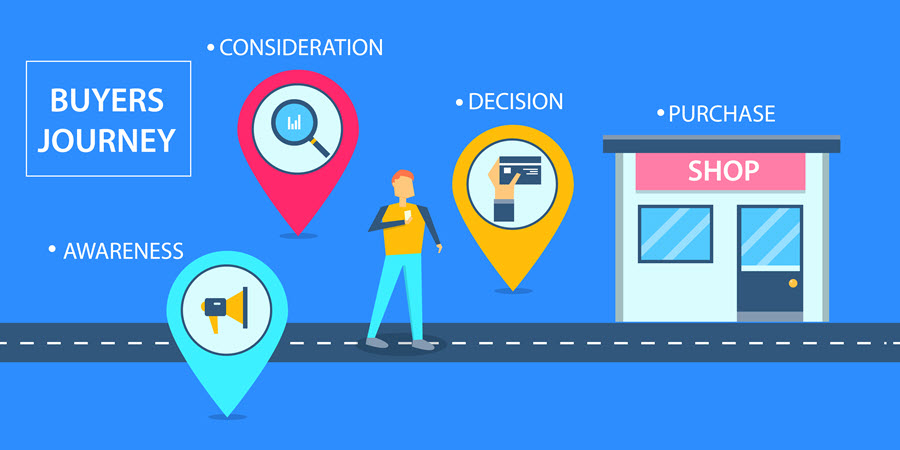
Social commerce shortens the buyer’s journey by providing a direct path from discovery to purchase. With just a few simple taps or clicks, users can make an order and go back to browsing and discovering more products to purchase.
What has made social commerce possible in the form we know it today are several key features that can be found on most social commerce platforms in 2024:
These and other features of social commerce platforms help shoppers, discover interesting products, make batter shopping decisions, and enjoy each and every step of the process.
They also help social media advertising platforms like Moontoast reach broader audiences. Even though Moontoast is no longer operational, the platform is a great example of an innovative advertising platform that explored the potential of social media, enabling enable brands and agencies to execute, manage, and track in real-time ad campaigns on sites like Facebook and Twitter.
In 2024, there are many competing social commerce platforms hoping to become major e-commerce hubs. When selecting a social commerce platform, it’s important to keep in mind that different platforms attract different types of users. While some products are “instagrammable,” others are not so much. Listed below are the top 7 best social commerce platforms all marketers, as well as avid shoppers, need to know about in 2024.
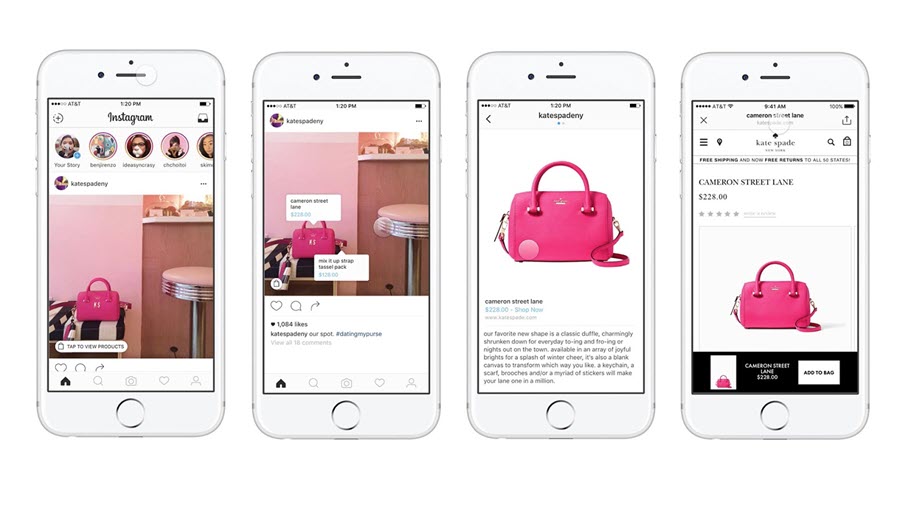
Boasting the highest average order value of all major social commerce platforms, Instagram is a force to be reckoned with. A long time before Facebook added the first e-commerce feature to Instagram, millions of shoppers had already been using the social media site for product discovery.
In March 2019, Instagram launched the long-awaited Checkout feature, creating an end-to-end in-app e-commerce experience. With Instagram Checkout, users can find an interesting product on Instagram and purchase it without ever leaving the site. Instagram Checkout even saves purchasing information, making future purchases even more seamless.
The Checkout feature can be seen as an extension of Shoppable Posts, which Instagram launched in 2018. Brands large and small use Shoppable Posts to tag products in content, transforming professional and user-generated content alike into shop windows.
Fashion products are by far the biggest sellers on Instagram, followed by beauty and lifestyle products. Generally, for a product to sell well on Instagram, it has to be visually appealing and priced just right to fall into the impulse-purchase category.
Facebook first jumped into the social commerce space with Facebook Page Shops, which allow businesses to easily set up a store within Facebook. To get started, a business owner has to click the Add Shop button, agree to merchant terms of service, enter payment processing details, and provide some information about the business and its products.
Some brands, such as high-end watch seller MVMT, have already experienced a lot of success with Facebook Page Shops. In the case of MVMT, the brand achieved approximately 60,000 unique visits to its store just 90 days after opening, converting 0.5 percent of visitors into paying customers and earning around $15,000 in revenue.
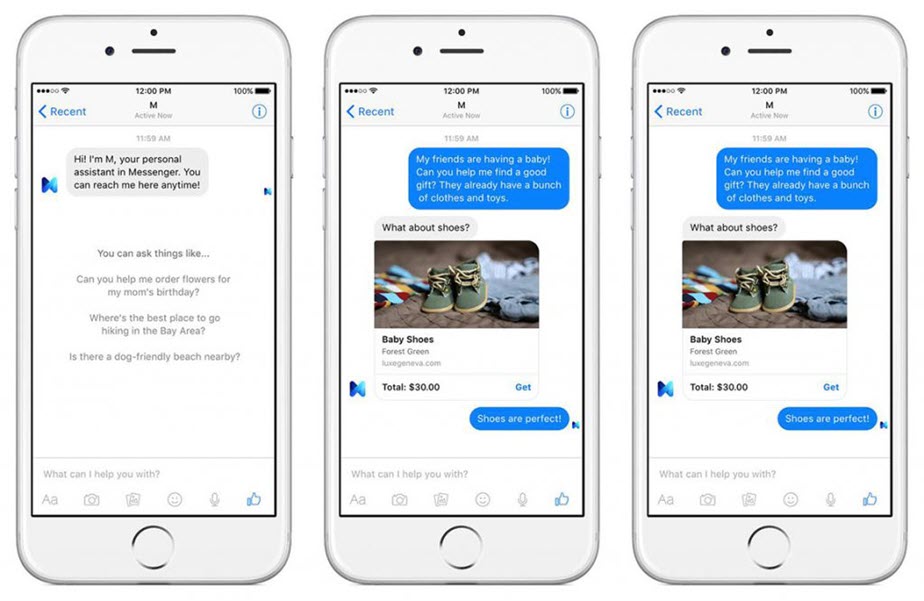
In addition to Facebook Page Shops, Facebook users can now also purchase products directly in the Messenger app while chatting with the store owner or an employee in real-time. Facebook is essentially allowing shoppers to walk into an online store, describe their problem to an employee, receive a product recommendation, and purchase the recommended product—all within the Messenger app.
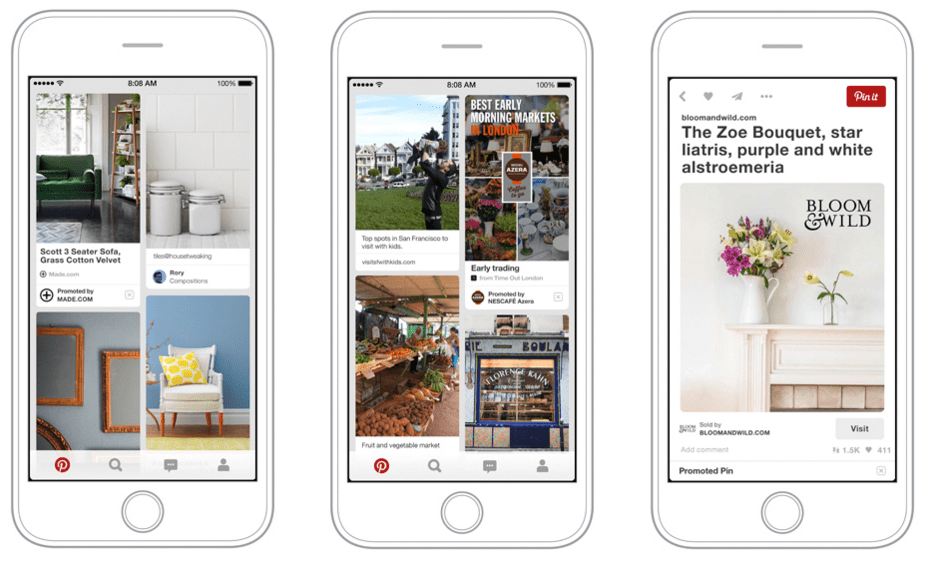
Buyable Pins have been with Pinterest users since 2015, enabling them to buy products without leaving the social bookmarking site. It’s estimated that the number of Buyable Pins reached 60 million only six months after their launch, which is a huge number considering that Pinterest has around 300 million users.
Since the introduction of Buyable Pins, Pinterest has also introduced Shop the Look and Catalogs. The former social commerce feature lets brands highlight products available for purchase in photos. When a Pinterest user stumbles upon a product he or she wants to buy, they can simply click on the product and be redirected to the brand’s website.
With Catalogs, brands can quickly upload their entire product catalogs to Pinterest, which automatically turns the raw product data into visually attractive pins. According to Pinterest’s own data, 83 percent of its users have made a purchase based on the content they saw from brands on the site.
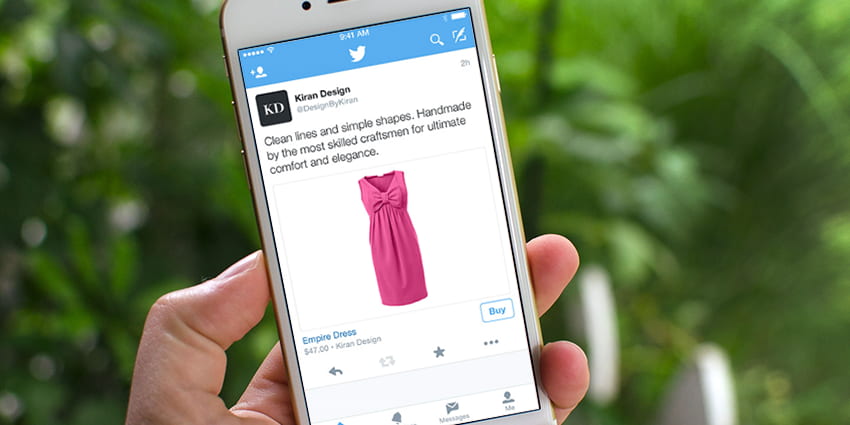
Twitter is an interesting example of a social commerce platform because its own users seem to resist social commerce. Shortly after the social media giant implemented its Buy button, Twitter users started protesting the new feature, arguing that it has no place on Twitter. After some time, Twitter decided to roll it back and abandon its plan to become a major player in the e-commerce industry.
But despite pivoting away from e-commerce, Twitter remains an extremely important marketing channel that allows brands to engage directly with their customers through ordinary and Promoted Tweets, which are displayed at the top of relevant search results pages on Twitter, in search results for a Promoted Trend, on the Timeline, on select user profiles, and in the official Twitter clients.
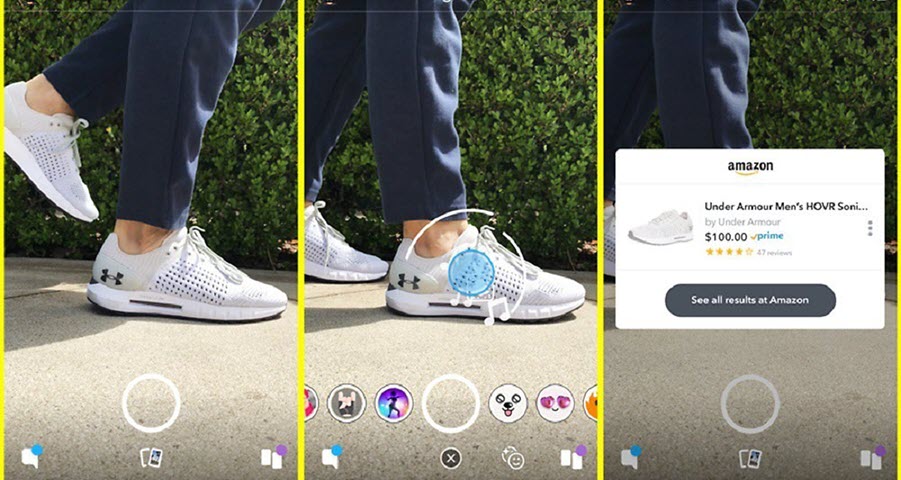
For Snapchat, social commerce has been a lifesaver. Before the company firmly decided to enter the e-commerce market, it had been struggling with a declining user base. In Q4 2018, revenues increased 36 percent to a record $390 million, largely thanks to its shift towards encouraging e-commerce. Today, social commerce lies at the heart of Snapchat, and the number of available social commerce features keeps increasing.
For some time now, Snapchat users have been enjoying a visual search feature that lets them find and purchase products on Amazon with the Snapchat app after scanning either the product itself or barcode. Brands and marketers can advertise on Snapchat with Shoppable Snap Ads, which let them feature a series of products that users can tap to get more details. Snapchat has also collaborated with several brands, such as Jordan and Levi’s.
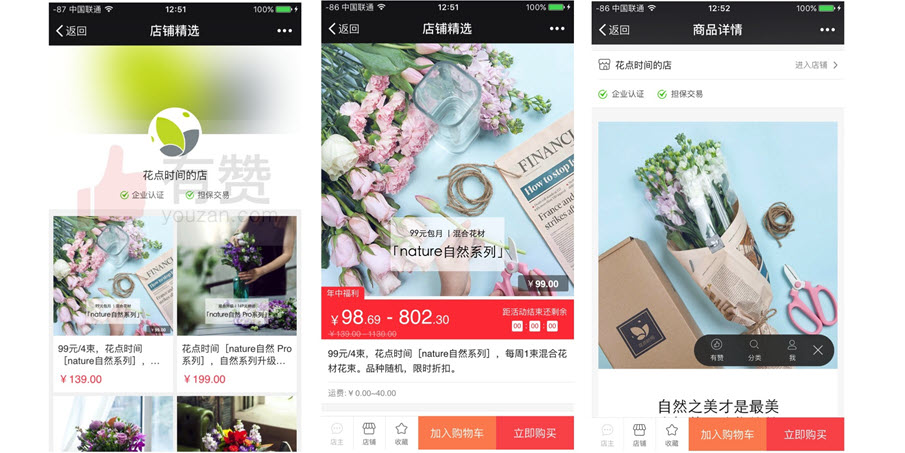
Developed by China’s tech giant Tencent Holdings, WeChat is a massively popular social media app with over 1 billion monthly active users. It can be said that WeChat is what Facebook Messenger aspires to become: a massive social hub with built-in support for mobile payments, video calls, scheduling, location sharing, games, and much more.
Merchants can spread awareness of their products through WeChat Moments, using this fundamental feature of WeChat to post text-based updates, upload up to nine images, and share videos and articles. They can create WeChat Official Accounts, which work more or less like Facebook Pages, allowing merchants to gather followers, send them push notifications, and redirect them to an external website. These features coupled with built-in mobile payments make WeChat and extremely powerful social commerce platform that most Western marketers have yet to explore.

With its global audience of around 500 million, the video-sharing social networking service TikTok could certainly become a dominant social commerce platform if it plays its cards right. Recently, TechCrunch and other websites announced TikTok’s plan to allow some users to add links to e-commerce sites to their profile biography and easily send their viewers to shopping websites.
“We’re always experimenting with new ways to improve the app experience for our users,” a spokesman for TikTok parent ByteDance told TechCrunch. “Ultimately, we’re focused on ways to inspire creativity, bring joy and add value for our community.”
This functionality certainly wouldn’t be groundbreaking as far as social commerce platforms go, but what separates TikTok from the likes of Facebook, Pinterest, Twitter, and even Instagram is the fact that its audience consists mostly of young people belonging to the Generation Z.